Tasks: Phishing Scams

Phishing scams are attempts to get you to reveal passwords or personal information that the scammers can abuse. Usually, the people behind phishing scams will try to get you to click on a link. This link may lead you to a site where you are asked to give away personal information, or it may upload malware to your device. Phishing scams may also attempt to get you to communicate with the scammer via email so that they can establish a personal relationship and get information that way.
In the box, you will see an example of a phising scam letter from 2014. Study the letter and point out four reasons to be suspicious of this letter.
Internal memo:
146 Hagley Road, Birmingham
Birmingham B3 3PJ
From the desk of Mr Jerry Smith
Date: 13/01/14
Attn: Sir / Madam
I seize the opportunity to extend my unalloyed compliments of the new season to you and your family hopping that this year will bring more joy, happiness, and prosperity into your house hold.
I am certain that by the time you read this letter I might already have gone back to my country United Kingdom. I visited South Africa during the New Year period and during my stay, I used the opportunity to send you this letter believing it will reach you in good state.
My name is Mr. Jerry Smith, I am the auditor and head of computing department of a bank here in United Kingdom. I wish to inform you of a bank account that was opened in our bank since my inception into office in 2001, and according to our record, it was evident that nobody had operated on this account since then. I therefore took the courage to look for a reliable and honest person who will be capable for this important transaction.
The owner of this money is Late Mr. Mutassim Billah Gaddafi, the son of late Muammar Gadafi of Libya; He was captured by anti-Gadafi forces and later killed alongside with his father. No other person knows about this money or anything concerning his account and the account has no next of kin and my investigation further proved to me that his family and his country does not know anything about this account.
I am therefore seeking for a reliable person that will play the human role as the next of kin to this fund which is in the amount of £ 32,000,000,00 (Thirty Two Million Pounds Sterling). I have also discovered that if I do not remit this money urgently, it will be forfeited to the government treasury account as an unclaimed fund.
Please respond immediately via my private email address: j_jerrysmith@aol.com
I will use my position and influence to effect the legal approval and onward transfer of this fund into any nominated bank account of your choice with appropriate clearance from foreign payment department.
You will henceforth stand to get 35% while 5% shall be set aside for the expense that will be incurred during the process, and 60% will be for me.
I will fill you in with further details upon your swift reply. Please be informed that confidentiality of this transaction is of utmost importance.
Yours truly
Mr. Jerry Smith
Source: Wikimedia Commons. Link to photo of the letter on Wikimedia Commons.
A letter like this one has tell-tale clues that warn most readers that something is not right. Research suggests that scammers include mistakes and exaggerations to target the most vulnerable. People who are not able to spot the red flags in this letter are unlikely to be able to take action against the scammers once they realise they have been defrauded.
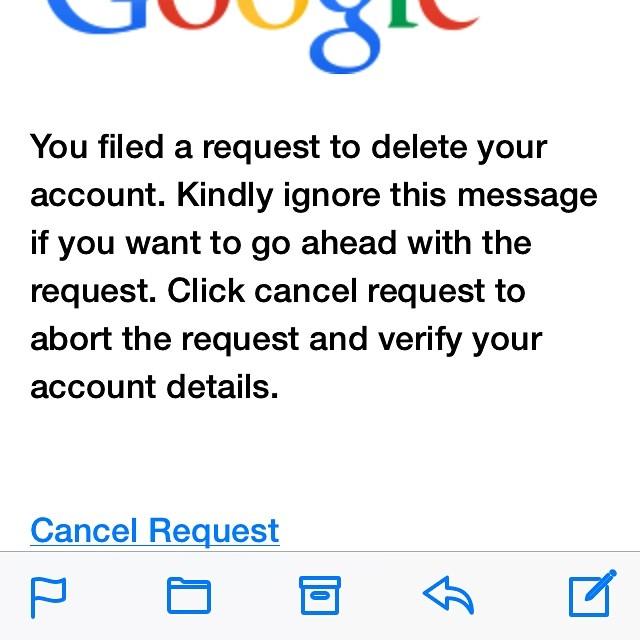
Unfortunately, not all scammers follow this strategy. In recent years, we have seen very sophisticated phishing scams that use email addresses, logos, advanced webdesigns, and other markers to convince the readers that the links are safe to engage with. This makes it much harder to spot a scam. For example, you may get an email from a streaming service you use, asking you to update your account. It may be an email that looks like it is coming from your bank, telling you that someone has attempted to withdraw a large sum of money and that you must click the link immediately to stop the transaction. Or it may look like a posting from a friend who is asking if this is really you in the video. Scammers have also found ways to misuse the phone numbers of real people to send out their scams, leaving the owner of the number shocked and confused as angry calls start streaming in.
The sophistication of these scams means that companies have had to develop new safety features when communicating with customers, and it means that communication online is slowed down as users are more inclined to check and double-check what they receive before engaging with it. Digital communication loses some of its immediacy when you have to call your boss to double check that they really want you to give out the information or click on the link they sent you. Phishing scams make online communication less seamless and more perilous.
Work in a group and discuss the questions below.
Do you think that, in the long term, phishing scams may threaten digital communication and force us to either return to phone calls and letters, or to develop new security measures or methods of communicating?
Are you good at spotting phishing scams?
Have you heard of anyone who has become the victim of a phishing scam? What happened?
Work with a partner and share your experiences with phishing scams.
Check the spam filter of your inbox: Do you find any attempted phishing scams there? If so, what are they, and what makes you suspicious?
Check your inbox. Has the spam filter successfully removed all phishing scams? If not, what got through, and why do you think it was not detected by the automated control?
Can you remember ever receiving phishing scams or suspicious posts on social media?
Have you ever received phishing scams as text messages on your phone?
Write a short text where you advise someone who is over 70 years old about how to avoid phishing scams.
Write a short text where you advise a child who is getting their first smart phone about how to spot phishing scams.
Several comedians have built routines around engaging with scammers online. Here, you can watch James Veitch's TED Talk about responding to a spam email. (There is a transcript of the talk below the video.)
Does this talk teach us anything about phishing scams?